n8n Credentials Explained: OAuth2, API Keys, Authentication & Setup (Key Concepts Part 6)
In previous parts of our series — Part 1,Part 2,Part 3,Part 4, and Part 5 — we explored the foundations of workflow automation in n8n: how to trigger workflows, transform and route data, and control flow with logic nodes.
Now in Part 6, we’re taking a big step forward by focusing on guide to verifying n8n credential — authenticating with external services and APIs using credentials like API keys and OAuth2.
Table of Contents
- Why Authenticating External APIs Matters
- Built-in Nodes vs. HTTP Requests
- n8n Credentials: Your API Key to the Kingdom
- How to Set Up and Use n8n Credentials
- Supported n8n Authentication Methods
- Security Best Practices for n8n Credentials
- Real-World Examples
- Pro Tips When Using HTTP APIs
- Frequently Asked Questions (FAQ)
- Wrapping Up
💡 Why Authenticating External APIs Matters
Most of us don’t work inside just one app. We rely on email tools, spreadsheets, CRMs, chat platforms, AI models, and more — and they rarely talk to each other by default.That’s where n8n’s credential system shines.
Imagine this:
- A user submits a form → their data gets stored in Google Sheets → your team is pinged on Slack → and they get a thank-you email.
- You get a new customer support message → the content is sent to GPT-4 to generate a draft reply → it gets auto-emailed.
- You’re syncing new orders from Shopify to Airtable to build a dashboard — with zero code.
Whether you’re using built-in integrations or crafting custom API requests, n8n can connect everything.
🔌 Built-in Nodes vs. HTTP Requests
You have two main options in n8n when working with external platforms:
🧰 1. Built-in Nodes
n8n provides prebuilt nodes for many popular services, including:
- Google Sheets – For reading, writing, or updating spreadsheets
- Slack – For sending notifications or messages
- OpenAI – For GPT-based text generation and chat automation
- Mailchimp – For managing email lists and campaigns
These nodes are great because they’re easy to configure and include built-in authentication support.
🌐 2. HTTP Request Node
When no native integration exists, the HTTP Request Node is your universal tool.
You can connect to nearly any third-party REST API using standard methods like GET, POST, PUT, and DELETE. It gives you full control over request headers, URLs, query strings, and payloads.
You can find more detailed information in our guide to the n8n HTTP Request Node, including tips for understanding common HTTP methods, handling APIs, authentication, and query parameters.
Once you’re ready to connect with external APIs, the most important part is authentication. Let’s break down the core methods n8n supports.
🔑 n8n Credentials: Your API Key to the Kingdom
No surprise here—most APIs won’t just let anyone in. You need to authenticate, and n8n supports all the popular methods you’d expect. Here’s a quick rundown of the most common types:
- 🔐 API Key – Easiest setup. Add it as a header. Works great with OpenAI, Mailchimp, etc.
- 🦮 OAuth2 – Secure and modern. Required for services like Google and GitHub.
- 🔑 Basic Auth – Simple username/password, used in many internal systems.
🤔 When to use OAuth2 vs API Key vs Basic Auth
| Method | Best For | Common Examples |
|---|---|---|
| API Key | Server-to-server communication or personal scripts where you have a simple, static secret. It’s direct and easy to implement. | OpenAI, Stripe, most modern SaaS APIs. |
| OAuth2 | Granting a third-party application (like n8n) limited, secure access to your data on another service on your behalf, without sharing your password. | Google (Sheets, Calendar), Slack, GitHub, HubSpot. |
| Basic Auth | Simple internal services, legacy systems, or APIs where high security is not the primary concern and you just need a username/password. | Internal company dashboards, routers, some older enterprise systems. |
Want to see the full list of authentication methods (including Query, Header, OAuth1, Digest, and more)?Jump to the Supported Authentication Methods below.
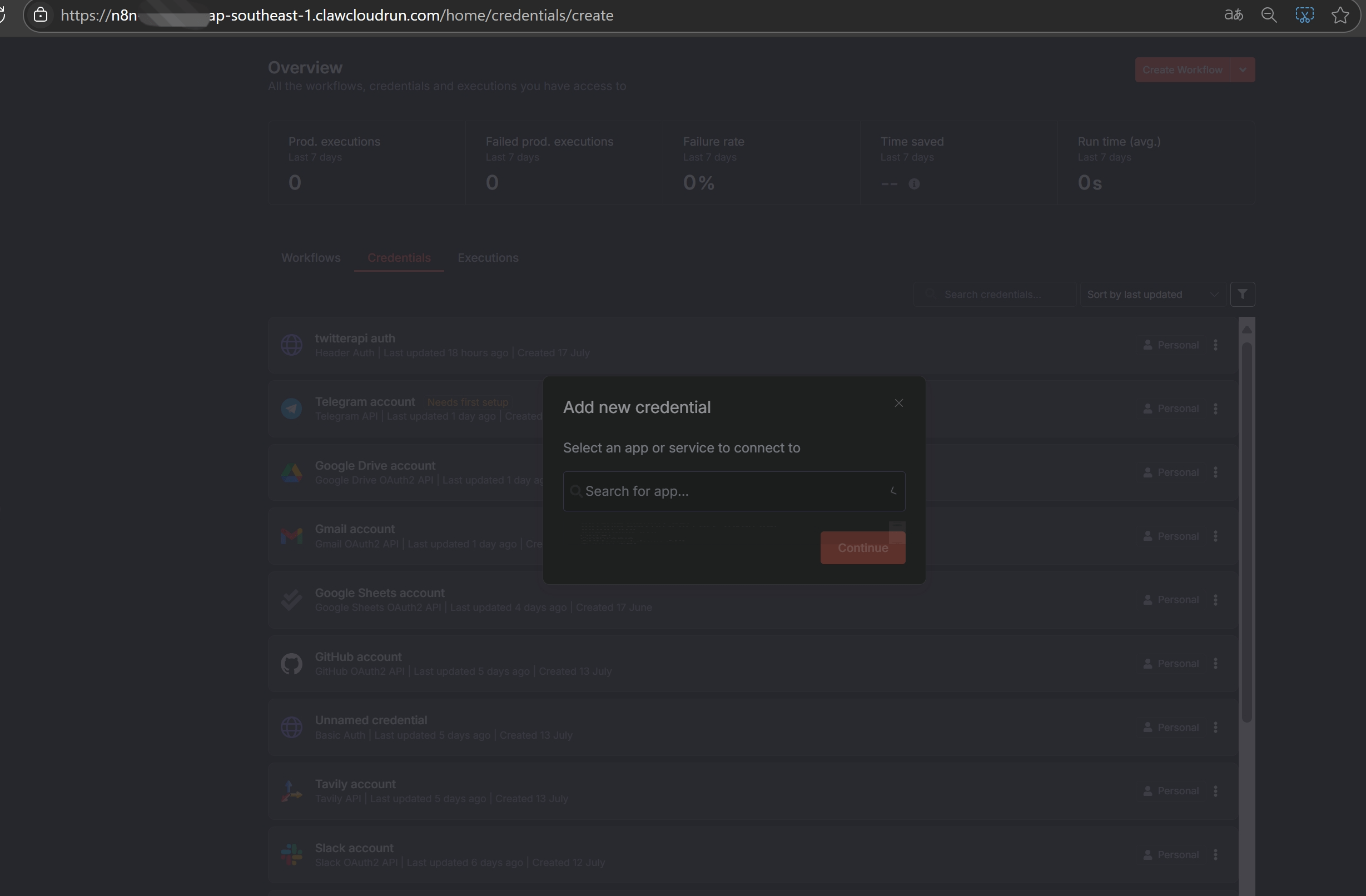
🗂️ How to Set Up and Use n8n Credentials
One of the best things about n8n is how it handles authentication. Instead of pasting API keys or tokens directly into every node, n8n uses a centralized credentials manager.
✅ Here’s how to set it up:
- Go to the Credentials tab in the left sidebar of n8n.
- Click “New Credential”, and choose the service or authentication method you need.
- Fill out the required fields—like API key, client ID/secret, scopes, or username/password.
- Save it and reuse it across any node that supports credentials.
🔐 Supported n8n Authentication Methods
n8n supports a wide range of authentication options, especially through the HTTP Request Node. Here are the most common methods with examples:
- API Key (Bearer Token) — Adds a token in the
Authorization: Bearerheader. This is a very common standard. - Header Auth — Sends credentials in a custom header. For example, the request would contain a header like this:
X-API-Key: 123abc-your-secret-key-here-456xyz - Query Auth — Adds credentials as parameters directly in the URL. The URL you call would look like this:
https://api.example.com/data?api_key=123abc-your-secret-key-here - Basic Auth — A simple, encoded username and password combination.
- OAuth2 — The most secure, modern flow for granting scoped permissions (supports token refresh).
- OAuth1 — Legacy support for older services.
- Digest Auth — For certain legacy or internal systems.
- Generic Credential Setup — Build your own header/query configuration using the flexible UI.
Using n8n’s credential system makes your workflows much easier to maintain, audit, and secure.
🛡️ Security Best Practices for n8n Credentials
Handling API keys and credentials is a serious responsibility. Here are some essential best practices to keep your automation secure:
Rotate Your API Keys Regularly
Just like changing your passwords, you should periodically rotate (generate a new one and delete the old one) your API keys. This limits the window of opportunity for misuse if a key is ever accidentally exposed. Set a calendar reminder every 6-12 months to audit and rotate the keys used in your n8n workflows.
Apply the Principle of Least Privilege
When you generate an API key or set up an OAuth2 app, only grant it the minimum permissions (scopes) necessary. For instance, if your workflow only needs to read data from a database, create a credential with read-only access. Never use a master key with full administrative privileges in a workflow unless it’s absolutely required.
Use Environment Variables for Your Encryption Key
For self-hosted n8n instances, your master N8N_ENCRYPTION_KEY is the most critical secret. This key should always be set as an environment variable in your server or Docker configuration, not hard-coded in a file. This practice separates your code and configuration from your secrets, which is a fundamental security principle.
Monitor Your API Usage
Periodically check the API usage dashboards provided by your services (e.g., Google Cloud Platform, OpenAI). Look for any unusual spikes in activity, which could be an early warning sign that a credential has been compromised and is being misused.
Real-World Examples
#1: Connect to GitHub with OAuth2
This example demonstrates how to use OAuth2 authentication with GitHub. This is useful if you want to automate pull request processing, repo insights, or team notifications.
📸 Visual Walkthrough: Registering a GitHub OAuth App
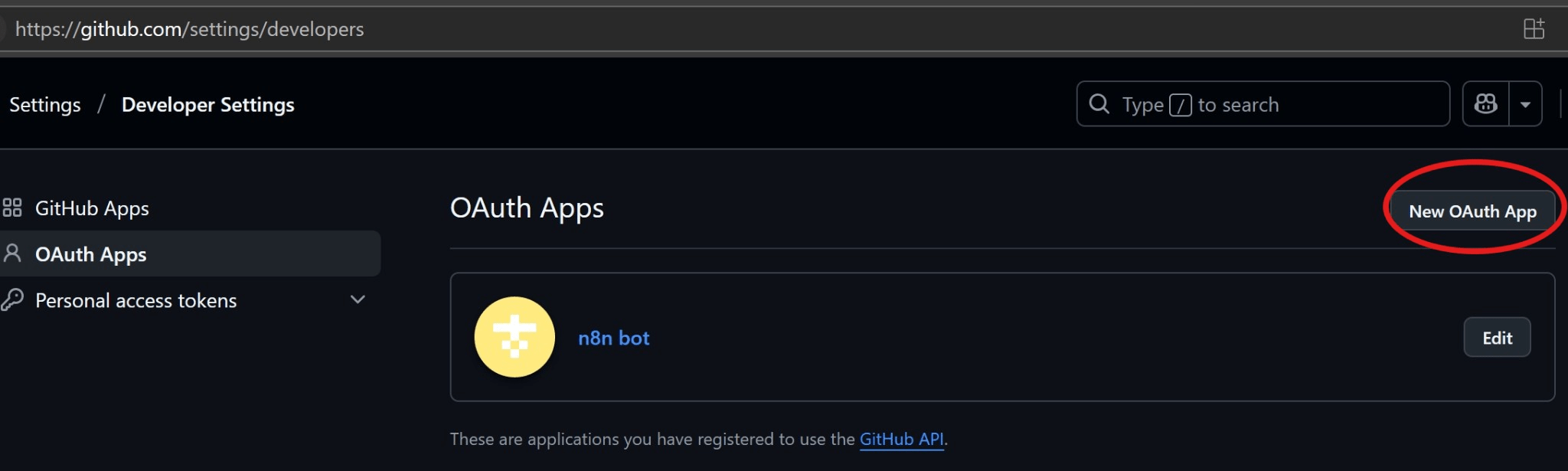
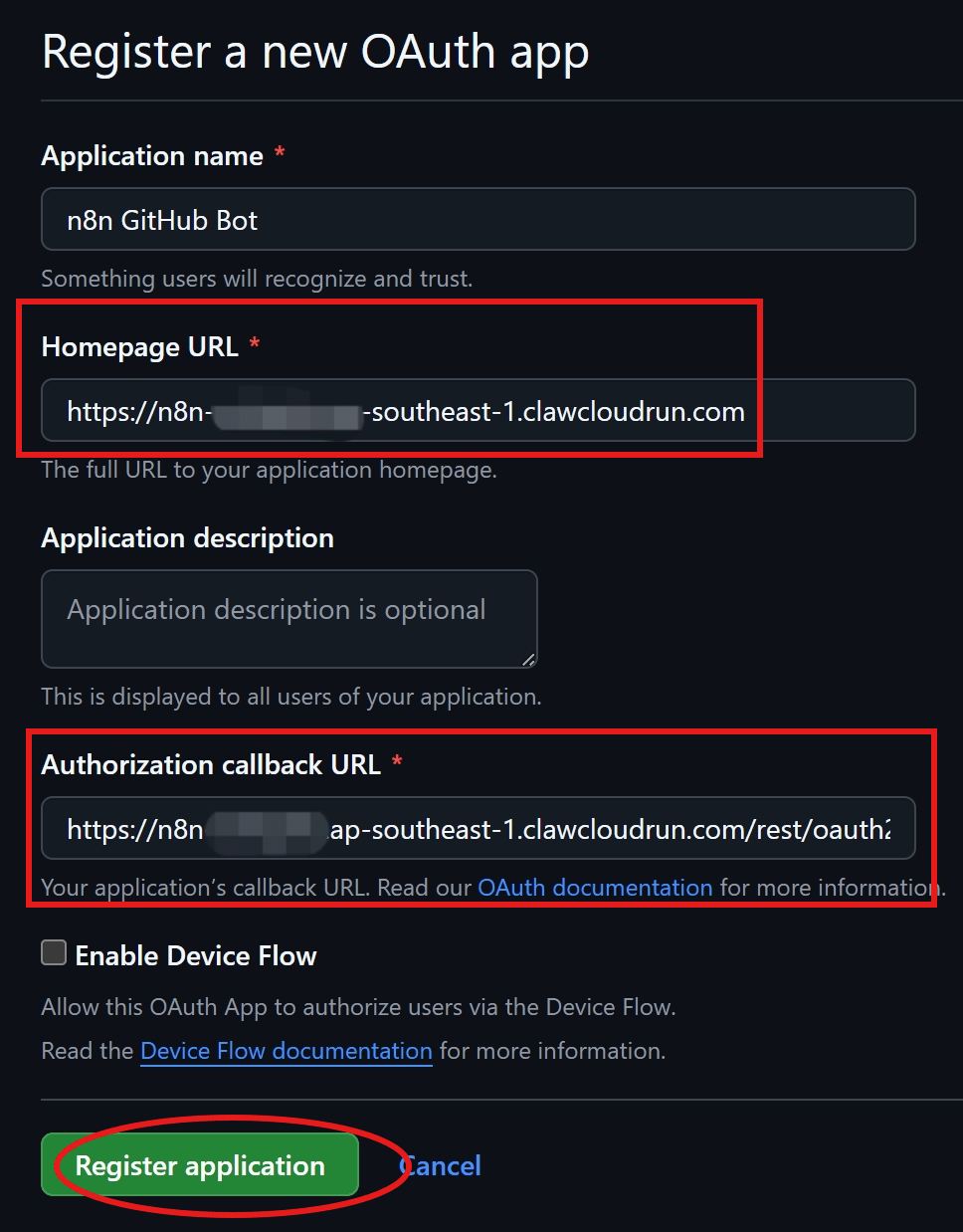
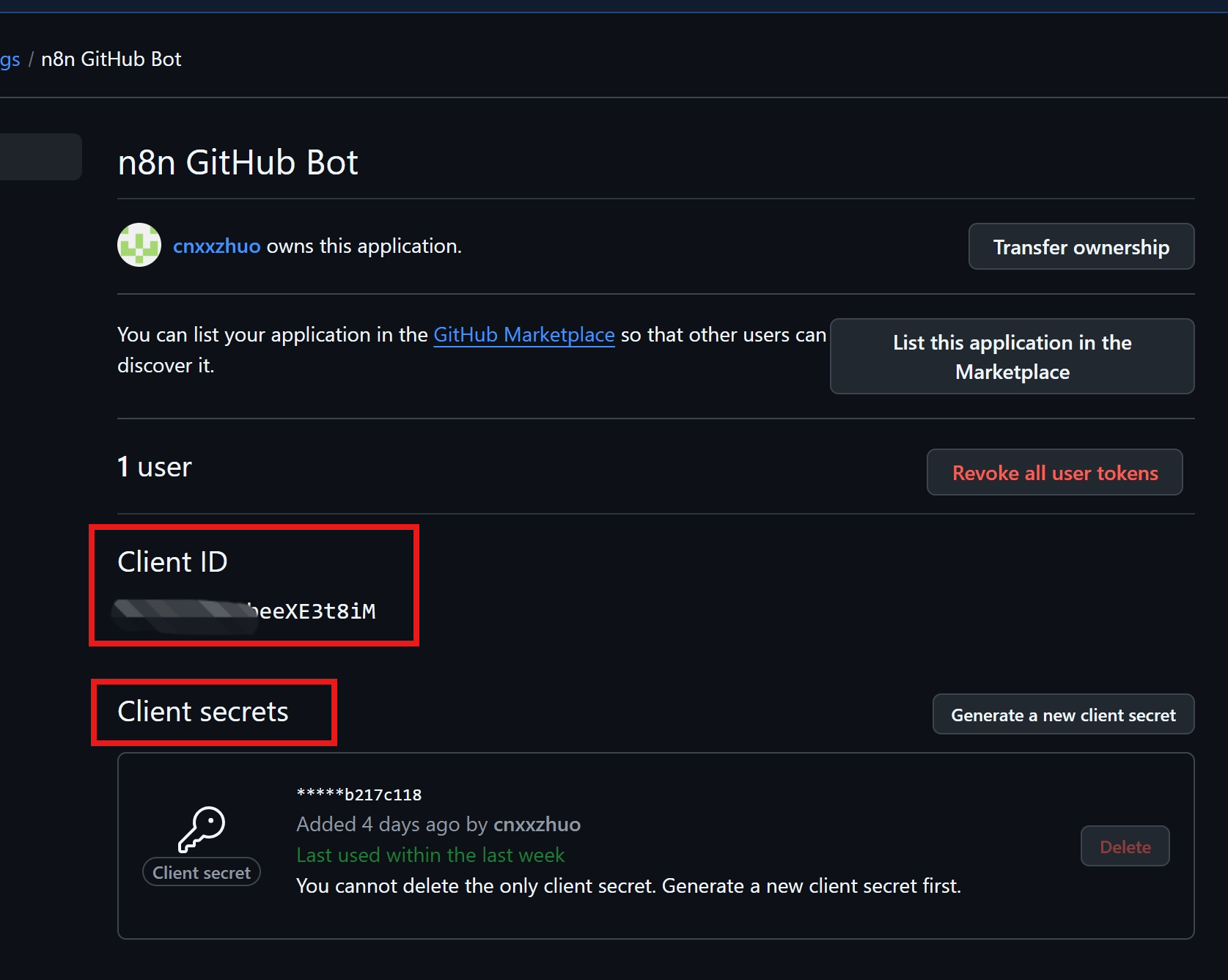
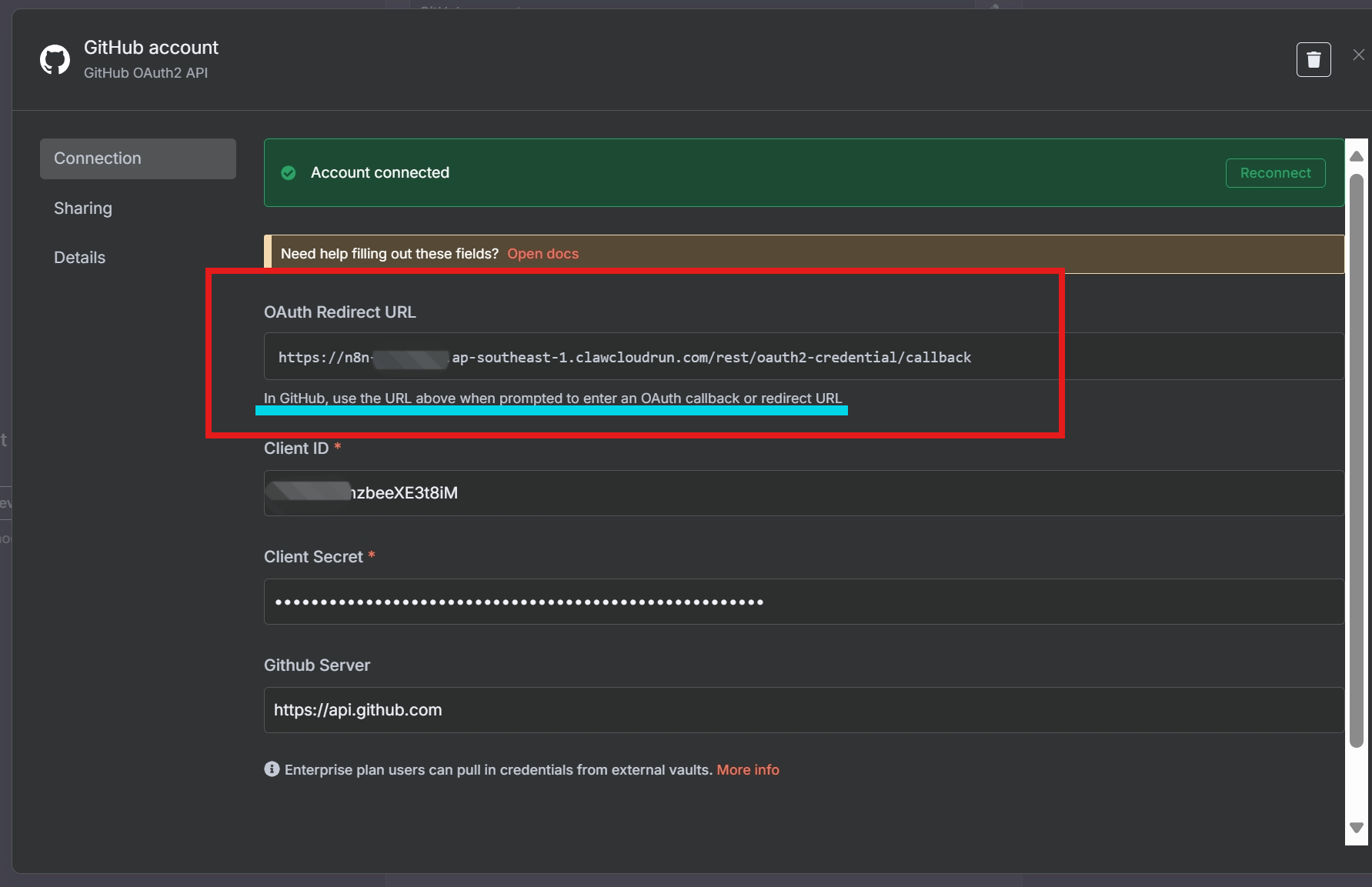
✅ Step-by-Step Summary
- Register a GitHub OAuth App with callback URL from n8n.
- Create a new OAuth2 Credential in n8n with GitHub endpoints and Client ID/Secret.
- Use HTTP Request Node to call GitHub API (e.g.,
https://api.github.com/user).
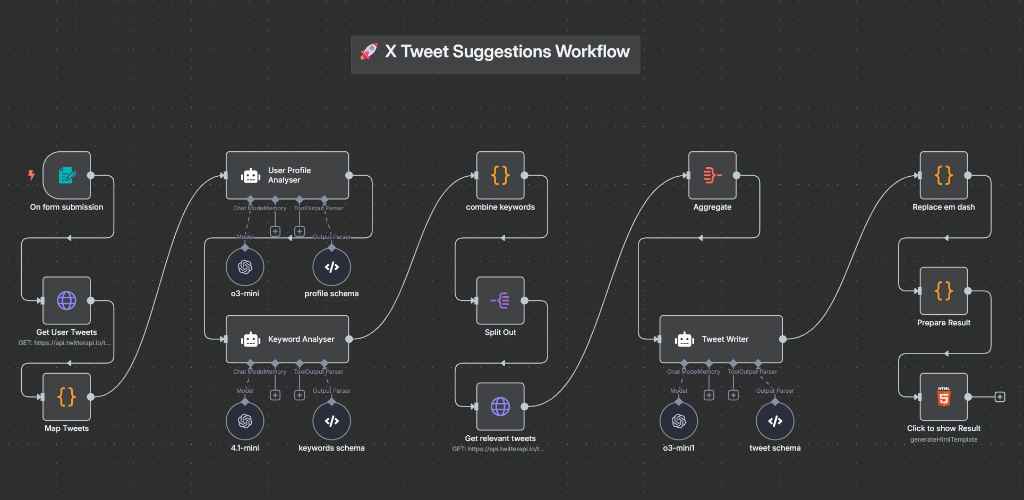
#2: AI-Powered Tweet Suggestions from Twitter API
Let’s now look at a practical use case that showcases exactly how to connect an API to n8n. In this example, n8n fetches real-time tweets from Twitter via an external API, analyzes them using a GPT model, and then generates intelligent, high-quality tweet suggestions. It demonstrates the full pipeline: authentication, data retrieval, processing, and output — all automated through one seamless workflow.
🔍 What This Workflow Does
- Analyze their past tweets.
- Understand trending topics in their niche.
- Generate strategic replies and original tweets using GPT.
🔐 Step 1: Set Up Twitter API Authentication (Header Auth)
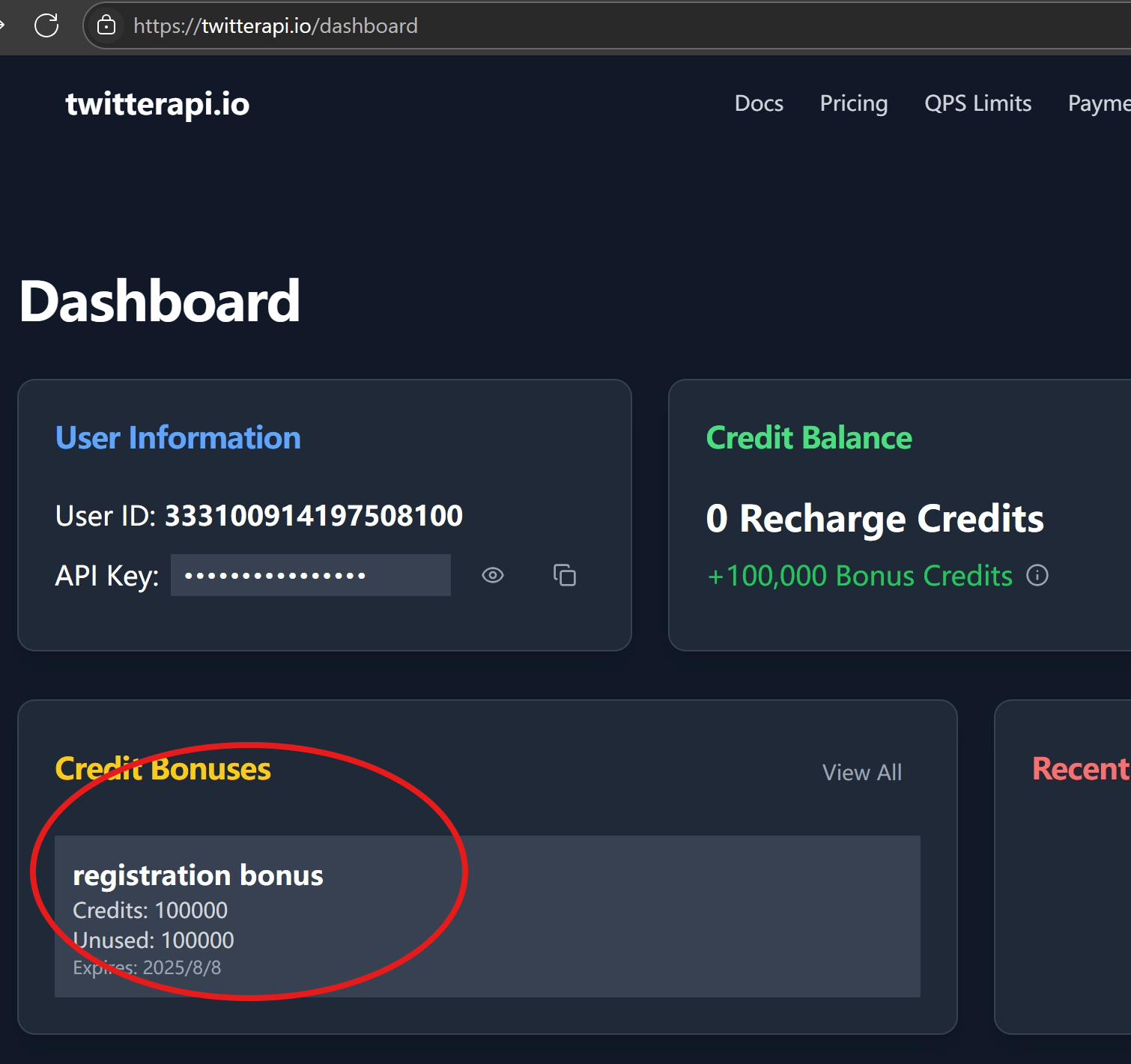
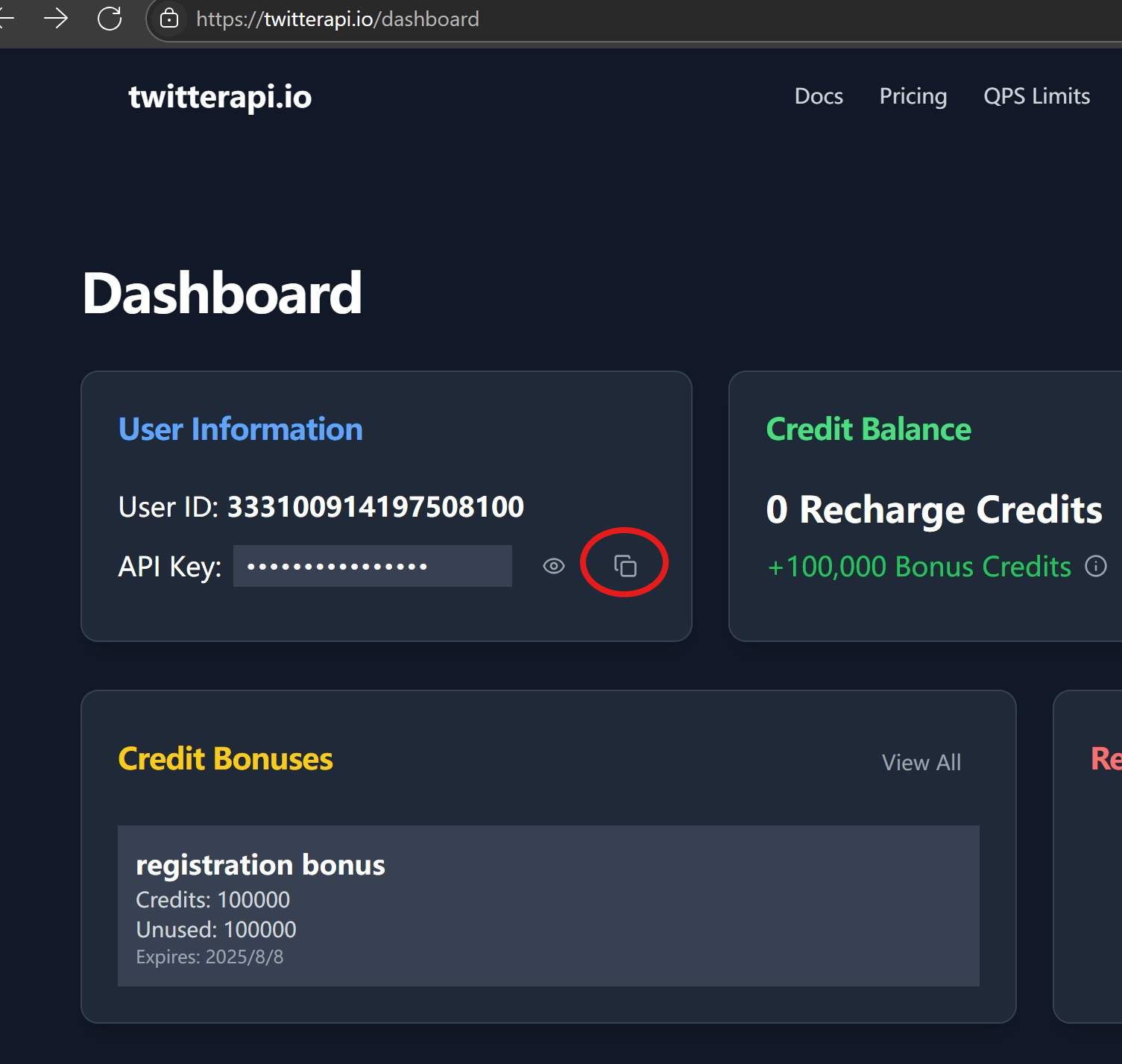
- Go to
twitterapi.io/dashboard - Copy your API Key
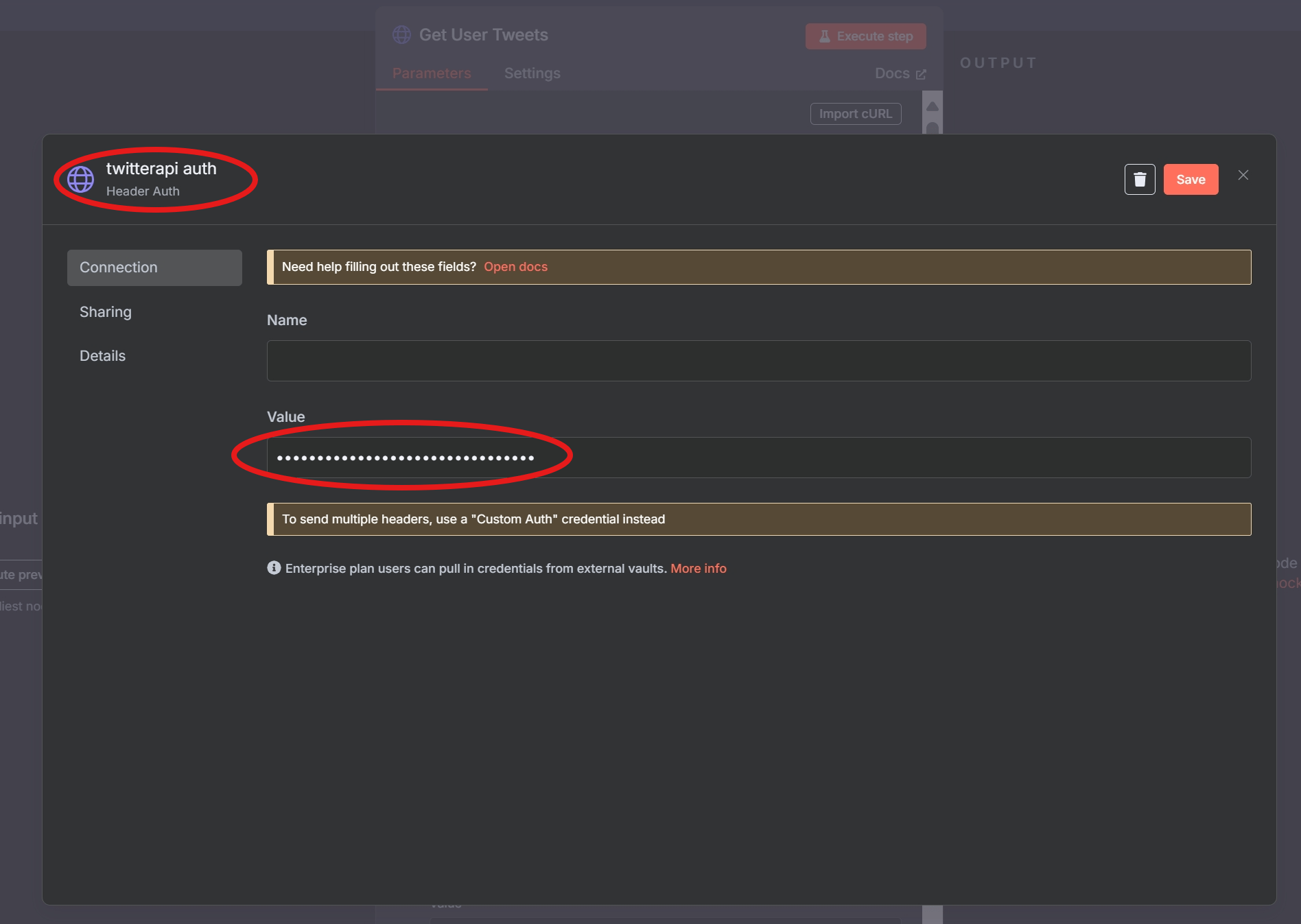
- In n8n → Credentials > New > HTTP Header Auth
- Name it
twitterapi auth, set header as:Authorization: <your-api-key>
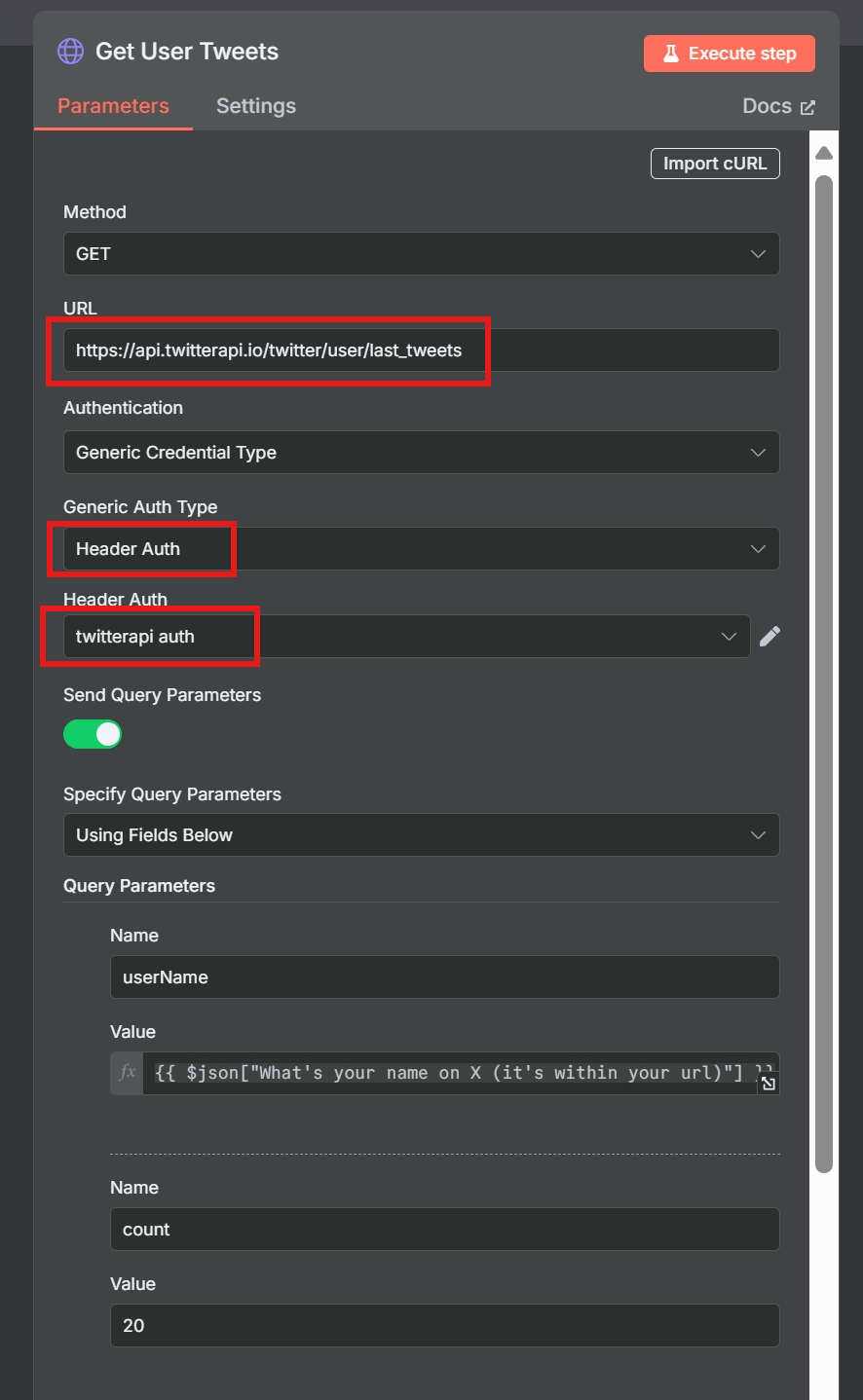
🔗 Step 2: HTTP Request Node – Get Recent Tweets
| Field | Value |
|---|---|
Method |
GET |
URL |
https://api.twitterapi.io/twitter/user/last_tweets |
Credential |
twitterapi auth |
Query Parameters |
"userName, count=20" |
⚡ Pro Tips When Using HTTP APIs in n8n
| Tip | Benefit |
|---|---|
| Use Credential Reuse | Don’t hardcode secrets — use Credentials Manager |
| Test APIs in Postman or curl | Debug responses before putting into production workflows |
| Combine with AI | Preprocess or enhance API data using LLMs or LangChain |
| Handle Rate Limits & Errors | Use “Wait, Retry, or Error Trigger node” |
| Parse Arrays Cleanly | Split Out + Aggregate help process list data like tweets |
🤔Frequently Asked Questions (FAQ)
What is the difference between an API Key and OAuth2 in n8n?
Think of an API Key as a single, fixed key to a door. You send this key with every request to prove your identity. It’s simple and works well for direct, server-to-server communication (like with OpenAI).
OAuth2 is more like a valet key that has specific permissions and an expiration date. Instead of giving n8n your main password, you grant it limited access to act on your behalf for a service like Google or GitHub. It’s a more secure and flexible standard for third-party application access.
How does n8n store credentials securely?
n8n encrypts all credentials before saving them to its database. This is done using a unique encryption key (N8N_ENCRYPTION_KEY) that you define when you set up your n8n instance. This means that even if someone accessed the database, your credentials would remain unreadable without your specific key.
Can I share n8n credentials between different workflows?
Yes, absolutely. That is the core benefit of n8n’s centralized credential manager. You create a credential once, and then you can select and reuse it in any node across all of your workflows. If an API key changes, you only need to update it in one place, and it will automatically apply everywhere it’s used.
